Using John the Ripper in Ubuntu 11.04 John the Ripper is a free password cracking software tool. Initially developed for the UNIX operating system, Firstly, install the package # apt-get install john Both unshadow and john distributed with - John the Ripper security software or fast password cracker software. $ john unshadowed Warning: detected hash type 'sha512crypt', but the string is also recognized as 'crypt' Use the '-format=crypt' option to force loading these as that type instead Using default input encoding: UTF-8 Loaded 2 password hashes with 2 different salts (sha512crypt, crypt(3) $6$ SHA512 128/128 SSE2 2x) Remaining 1 password hash. Apr 19, 2017 If john -show=left is run against a file with no hashes cracked yet, john will print statistics but will not print any password hashes. Only if at least one hash has been cracked will john print the remaining hashes from the file like it's supposed to. Tested against john 1.8.0-jumbo-1-5603-g70e8d4c+.
John the Ripper is a free password cracking software tool. Initially developed for the UNIX operating system,
Firstly, install the package
# apt-get install john
Both unshadow and john distributed with – John the Ripper security software or fast password cracker software. It is free and Open Source software. It runs on Windows, UNIX and Linux operating system. Use this tool to find out weak users passwords on your own server.
John can work in the following modes:
[a] Wordlist : John will simply use a file with a list of words that will be checked against the passwords. See RULES for the format of wordlist files.
[b] Single crack : In this mode, john will try to crack the password using the login/GECOS information as passwords.
[c] Incremental : This is the most powerful mode. John will try any character combination to resolve the password. Details about these modes can be found in the MODES file in john’s documentation, including how to define your own cracking methods.
The unshadow tool combines the passwd and shadow files so John can use
them. You might need this since if you only used your shadow file, the
GECOS information wouldn’t be used by the “single crack” mode, and also
you wouldn’t be able to use the ‘-shells’ option. On a normal system
you’ll need to run unshadow as root to be able to read the shadow file.
# unshadow /etc/passwd /etc/shadow > crack.password.db
To check weak password (crack password), enter the following command
To use John, you just need to supply it a password file created using unshadow command along with desired options. If no mode is specified, john will try “single” first, then “wordlist” and finally “incremental” password cracking methods
# john crack.password.db
Created directory: /root/.john
No password hashes loaded
# john -show crack.password.db
0 password hashes cracked, 0 left
Alright the preceeding output shows that john the ripper (JTR) did not work and after readings in the Internet, I found the explanation:
John the Ripper (JtR) is available from Ubuntu repository, as well as open wall website: http://www.openwall.com/john/. However, none of them works on Ubuntu 9.04 and above due to the lack of support to sha-512 encryption. They give error “No password hashes loaded”.
Life Experience
How to know what encrytion is being used to protect the shadow password.
To know what encrytion is being used in your shadow password, type the following command:
#cat /etc/shadow

Look at the second field, which begins with the $ sign. Let’s say it begins with $6, your system uses sha512 encrytion. The following list will suggest what encrytion is used by your Linux distribution.
$1$ md5
$5$ sha256
$6$ sha512
Download John the Ripper
Download the package by typing:
wget www.openwall.com/john/g/john-1.7.8.tar.gz
wget www.openwall.com/john/g/john-1.7.8.tar.gz.sign
Unzip, patch and compile the program
#tar -zxvf john-1.7.8.tar.gz
#cd john-1.7.8
The patch lets “john” call crypt(3) to encode passwords when it sees unsupported encryption. There are 3 files we need to change/create: Makefile, crypt_fmt.c and john.c.
Append “-lcrypt” to line “LDFLAGS = -s”, making the line reads as:

Create file crypt_fmt.c:
Finally add two lines (Red) to john.c
and
Lastly run the make command
# make linux-x86-sse2
If your Linux is a 64 bit, type:
You should have “john” in ../run directory.
Run the John the Ripper
On Linux, the actual password is /etc/shadow not /etc/passwd. This file is readable to root user only and not readable to normal users. So copy it and change the read permission.
sudo unshadow /etc/passwd /etc/shadow> shadowfile
Or copy /etc/shadow as shadowfile and change the file to readable.
root@googlerunslinux:~/script/john-1.7.8/run# unshadow /etc/passwd /etc/shadow > crack.password.db
root@googlerunslinux:~/script/john-1.7.8/run# ls
all.chr crack.password.db john.conf password.lst unshadow
alnum.chr digits.chr lanman.chr unafs
alpha.chr john mailer unique
Then copy this file to the run directory of a computer with JtR we just compiled and run:
Press any key for progress, ^C for interruption.
To resume cracking from interruption, under run directory
John The Ripper 0 Password Hashes Cracked 1 Left Hand Piano
To show the cracked password(s)
root@googlerunslinux:~/script/john-1.7.8/run# ./john crack.password.db
Loaded 6 password hashes with 6 different salts (generic crypt(3) [?/32])
123 (razali)
123 (ken)
123 (ismail)
123 (shoutcast)
guesses: 4 time: 0:00:04:34 4% (2) c/
root@googlerunslinux:~/script/john-1.7.8/run# ./john –show
Password files required, but none specified
root@googlerunslinux:~/script/john-1.7.8/run# ./john –show crack.password.db
ismail:123:1000:1000:ismail,:/home/ismail:/bin/bash
shoutcast:123:1001:1001:shoutcast,:/home/shoutcast:/bin/bash
ken:123:1003:1003:ken,:/home/ken:/bin/bash
razali:123:1004:1004:,:/home/razali:/bin/bash
4 password hashes cracked, 2 left
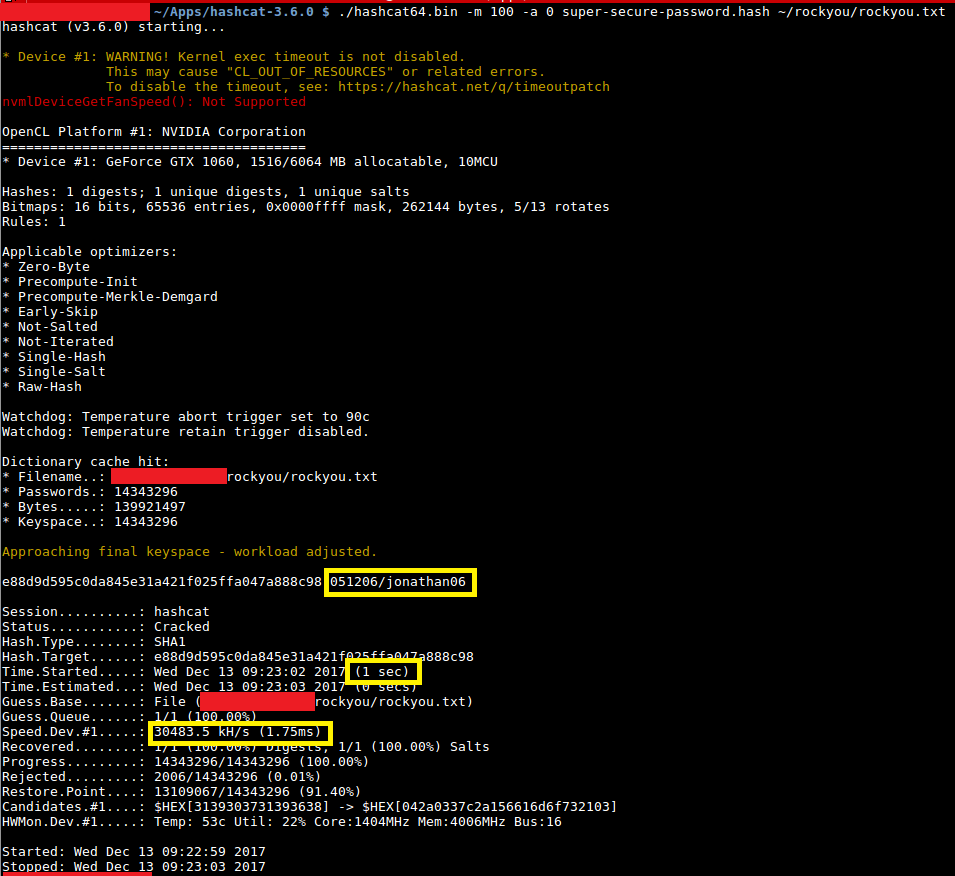
Another exercise
John The Ripper 0 Password Hashes Cracked 1 Left Hand
Now copy a username and its shadow password from the /etc/shadow file
I chose one user called ismail. I copied the account details to a file called tobecracked.txt. This is how the file look like.
# more tobecracked.txt
John The Ripper 0 Password Hashes Cracked 1 Left Hand Free
ismail:$6$RmhDju6G$YjLM2yVEoKyOIHaoHYXme3XD7fxfLAddEGZvNyPUSSD0l22RcXfTDx7zQugX6DKkYouPqX9LBPw6X0jZitIb/1:15280:0:99999:7:::
root@googlerunslinux:~/script/john-1.7.8/run#
Next run john and pass the password.lst file
root@googlerunslinux:~/script/john-1.7.8/run# ./john -w:password.lst tobecracked.txt
Loaded 1 password hash (generic crypt(3) [?/32])
money (ismail)
guesses: 1 time: 0:00:00:02 100% c/s: 45.07 trying: 12345 – missy
Use the “–show” option to display all of the cracked passwords reliably
John The Ripper 0 Password Hashes Cracked 1 Left Hand Grips
root@googlerunslinux:~/script/john-1.7.8/run# ./john –show tobecracked.txt
John The Ripper 0 Password Hashes Cracked 1 Left Hand 2
ismail:money:15280:0:99999:7:::
Windows Password Hashes
1 password hash cracked, 0 left
John successfully craked the password.
Comments are closed.